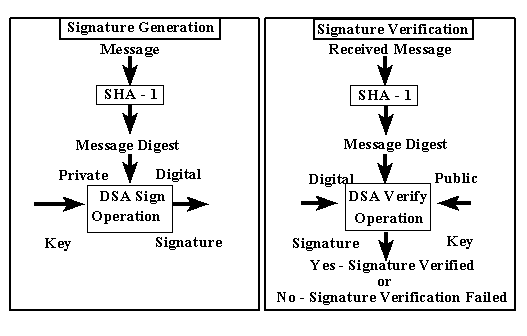
Figure 1: Using the SHA-1 with the DSA

X ^ Y = bitwise logical "and" of X and Y.
X \/ Y = bitwise logical "inclusive-or" of X and Y.
X XOR Y = bitwise logical "exclusive-or" of X and Y.
~ X = bitwise logical "complement" of X.
01101100101110011101001001111011
XOR 01100101110000010110100110110111
--------------------------------
= 00001001011110001011101111001100
A B C D E
t = 0: 0116FC33 67452301 7BF36AE2 98BADCFE 10325476
t = 1: 8990536D 0116FC33 59D148C0 7BF36AE2 98BADCFE
t = 2: A1390F08 8990536D C045BF0C 59D148C0 7BF36AE2
t = 3: CDD8E11B A1390F08 626414DB C045BF0C 59D148C0
t = 4: CFD499DE CDD8E11B 284E43C2 626414DB C045BF0C
t = 5: 3FC7CA40 CFD499DE F3763846 284E43C2 626414DB
t = 6: 993E30C1 3FC7CA40 B3F52677 F3763846 284E43C2
t = 7: 9E8C07D4 993E30C1 0FF1F290 B3F52677 F3763846
t = 8: 4B6AE328 9E8C07D4 664F8C30 0FF1F290 B3F52677
t = 9: 8351F929 4B6AE328 27A301F5 664F8C30 0FF1F290
t = 10: FBDA9E89 8351F929 12DAB8CA 27A301F5 664F8C30
t = 11: 63188FE4 FBDA9E89 60D47E4A 12DAB8CA 27A301F5
t = 12: 4607B664 63188FE4 7EF6A7A2 60D47E4A 12DAB8CA
t = 13: 9128F695 4607B664 18C623F9 7EF6A7A2 60D47E4A
t = 14: 196BEE77 9128F695 1181ED99 18C623F9 7EF6A7A2
t = 15: 20BDD62F 196BEE77 644A3DA5 1181ED99 18C623F9
t = 16: 4E925823 20BDD62F C65AFB9D 644A3DA5 1181ED99
t = 17: 82AA6728 4E925823 C82F758B C65AFB9D 644A3DA5
t = 18: DC64901D 82AA6728 D3A49608 C82F758B C65AFB9D
t = 19: FD9E1D7D DC64901D 20AA99CA D3A49608 C82F758B
t = 20: 1A37B0CA FD9E1D7D 77192407 20AA99CA D3A49608
t = 21: 33A23BFC 1A37B0CA 7F67875F 77192407 20AA99CA
t = 22: 21283486 33A23BFC 868DEC32 7F67875F 77192407
t = 23: D541F12D 21283486 0CE88EFF 868DEC32 7F67875F
t = 24: C7567DC6 D541F12D 884A0D21 0CE88EFF 868DEC32
t = 25: 48413BA4 C7567DC6 75507C4B 884A0D21 0CE88EFF
t = 26: BE35FBD5 48413BA4 B1D59F71 75507C4B 884A0D21
t = 27: 4AA84D97 BE35FBD5 12104EE9 B1D59F71 75507C4B
t = 28: 8370B52E 4AA84D97 6F8D7EF5 12104EE9 B1D59F71
t = 29: C5FBAF5D 8370B52E D2AA1365 6F8D7EF5 12104EE9
t = 30: 1267B407 C5FBAF5D A0DC2D4B D2AA1365 6F8D7EF5
t = 31: 3B845D33 1267B407 717EEBD7 A0DC2D4B D2AA1365
t = 32: 046FAA0A 3B845D33 C499ED01 717EEBD7 A0DC2D4B
t = 33: 2C0EBC11 046FAA0A CEE1174C C499ED01 717EEBD7
t = 34: 21796AD4 2C0EBC11 811BEA82 CEE1174C C499ED01
t = 35: DCBBB0CB 21796AD4 4B03AF04 811BEA82 CEE1174C
t = 36: 0F511FD8 DCBBB0CB 085E5AB5 4B03AF04 811BEA82
t = 37: DC63973F 0F511FD8 F72EEC32 085E5AB5 4B03AF04
t = 38: 4C986405 DC63973F 03D447F6 F72EEC32 085E5AB5
t = 39: 32DE1CBA 4C986405 F718E5CF 03D447F6 F72EEC32
t = 40: FC87DEDF 32DE1CBA 53261901 F718E5CF 03D447F6
t = 41: 970A0D5C FC87DEDF 8CB7872E 53261901 F718E5CF
t = 42: 7F193DC5 970A0D5C FF21F7B7 8CB7872E 53261901
t = 43: EE1B1AAF 7F193DC5 25C28357 FF21F7B7 8CB7872E
t = 44: 40F28E09 EE1B1AAF 5FC64F71 25C28357 FF21F7B7
t = 45: 1C51E1F2 40F28E09 FB86C6AB 5FC64F71 25C28357
t = 46: A01B846C 1C51E1F2 503CA382 FB86C6AB 5FC64F71
t = 47: BEAD02CA A01B846C 8714787C 503CA382 FB86C6AB
t = 48: BAF39337 BEAD02CA 2806E11B 8714787C 503CA382
t = 49: 120731C5 BAF39337 AFAB40B2 2806E11B 8714787C
t = 50: 641DB2CE 120731C5 EEBCE4CD AFAB40B2 2806E11B
t = 51: 3847AD66 641DB2CE 4481CC71 EEBCE4CD AFAB40B2
t = 52: E490436D 3847AD66 99076CB3 4481CC71 EEBCE4CD
t = 53: 27E9F1D8 E490436D 8E11EB59 99076CB3 4481CC71
t = 54: 7B71F76D 27E9F1D8 792410DB 8E11EB59 99076CB3
t = 55: 5E6456AF 7B71F76D 09FA7C76 792410DB 8E11EB59
t = 56: C846093F 5E6456AF 5EDC7DDB 09FA7C76 792410DB
t = 57: D262FF50 C846093F D79915AB 5EDC7DDB 09FA7C76
t = 58: 09D785FD D262FF50 F211824F D79915AB 5EDC7DDB
t = 59: 3F52DE5A 09D785FD 3498BFD4 F211824F D79915AB
t = 60: D756C147 3F52DE5A 4275E17F 3498BFD4 F211824F
t = 61: 548C9CB2 D756C147 8FD4B796 4275E17F 3498BFD4
t = 62: B66C020B 548C9CB2 F5D5B051 8FD4B796 4275E17F
t = 63: 6B61C9E1 B66C020B 9523272C F5D5B051 8FD4B796
t = 64: 19DFA7AC 6B61C9E1 ED9B0082 9523272C F5D5B051
t = 65: 101655F9 19DFA7AC 5AD87278 ED9B0082 9523272C
t = 66: 0C3DF2B4 101655F9 0677E9EB 5AD87278 ED9B0082
t = 67: 78DD4D2B 0C3DF2B4 4405957E 0677E9EB 5AD87278
t = 68: 497093C0 78DD4D2B 030F7CAD 4405957E 0677E9EB
t = 69: 3F2588C2 497093C0 DE37534A 030F7CAD 4405957E
t = 70: C199F8C7 3F2588C2 125C24F0 DE37534A 030F7CAD
t = 71: 39859DE7 C199F8C7 8FC96230 125C24F0 DE37534A
t = 72: EDB42DE4 39859DE7 F0667E31 8FC96230 125C24F0
t = 73: 11793F6F EDB42DE4 CE616779 F0667E31 8FC96230
t = 74: 5EE76897 11793F6F 3B6D0B79 CE616779 F0667E31
t = 75: 63F7DAB7 5EE76897 C45E4FDB 3B6D0B79 CE616779
t = 76: A079B7D9 63F7DAB7 D7B9DA25 C45E4FDB 3B6D0B79
t = 77: 860D21CC A079B7D9 D8FDF6AD D7B9DA25 C45E4FDB
t = 78: 5738D5E1 860D21CC 681E6DF6 D8FDF6AD D7B9DA25
t = 79: 42541B35 5738D5E1 21834873 681E6DF6 D8FDF6AD.
Block 1 has been processed. The values of {Hi} are
A B C D E
t = 0: 0116FC17 67452301 7BF36AE2 98BADCFE 10325476
t = 1: EBF3B452 0116FC17 59D148C0 7BF36AE2 98BADCFE
t = 2: 5109913A EBF3B452 C045BF05 59D148C0 7BF36AE2
t = 3: 2C4F6EAC 5109913A BAFCED14 C045BF05 59D148C0
t = 4: 33F4AE5B 2C4F6EAC 9442644E BAFCED14 C045BF05
t = 5: 96B85189 33F4AE5B 0B13DBAB 9442644E BAFCED14
t = 6: DB04CB58 96B85189 CCFD2B96 0B13DBAB 9442644E
t = 7: 45833F0F DB04CB58 65AE1462 CCFD2B96 0B13DBAB
t = 8: C565C35E 45833F0F 36C132D6 65AE1462 CCFD2B96
t = 9: 6350AFDA C565C35E D160CFC3 36C132D6 65AE1462
t = 10: 8993EA77 6350AFDA B15970D7 D160CFC3 36C132D6
t = 11: E19ECAA2 8993EA77 98D42BF6 B15970D7 D160CFC3
t = 12: 8603481E E19ECAA2 E264FA9D 98D42BF6 B15970D7
t = 13: 32F94A85 8603481E B867B2A8 E264FA9D 98D42BF6
t = 14: B2E7A8BE 32F94A85 A180D207 B867B2A8 E264FA9D
t = 15: 42637E39 B2E7A8BE 4CBE52A1 A180D207 B867B2A8
t = 16: 6B068048 42637E39 ACB9EA2F 4CBE52A1 A180D207
t = 17: 426B9C35 6B068048 5098DF8E ACB9EA2F 4CBE52A1
t = 18: 944B1BD1 426B9C35 1AC1A012 5098DF8E ACB9EA2F
t = 19: 6C445652 944B1BD1 509AE70D 1AC1A012 5098DF8E
t = 20: 95836DA5 6C445652 6512C6F4 509AE70D 1AC1A012
t = 21: 09511177 95836DA5 9B111594 6512C6F4 509AE70D
t = 22: E2B92DC4 09511177 6560DB69 9B111594 6512C6F4
t = 23: FD224575 E2B92DC4 C254445D 6560DB69 9B111594
t = 24: EEB82D9A FD224575 38AE4B71 C254445D 6560DB69
t = 25: 5A142C1A EEB82D9A 7F48915D 38AE4B71 C254445D
t = 26: 2972F7C7 5A142C1A BBAE0B66 7F48915D 38AE4B71
t = 27: D526A644 2972F7C7 96850B06 BBAE0B66 7F48915D
t = 28: E1122421 D526A644 CA5CBDF1 96850B06 BBAE0B66
t = 29: 05B457B2 E1122421 3549A991 CA5CBDF1 96850B06
t = 30: A9C84BEC 05B457B2 78448908 3549A991 CA5CBDF1
t = 31: 52E31F60 A9C84BEC 816D15EC 78448908 3549A991
t = 32: 5AF3242C 52E31F60 2A7212FB 816D15EC 78448908
t = 33: 31C756A9 5AF3242C 14B8C7D8 2A7212FB 816D15EC
t = 34: E9AC987C 31C756A9 16BCC90B 14B8C7D8 2A7212FB
t = 35: AB7C32EE E9AC987C 4C71D5AA 16BCC90B 14B8C7D8
t = 36: 5933FC99 AB7C32EE 3A6B261F 4C71D5AA 16BCC90B
t = 37: 43F87AE9 5933FC99 AADF0CBB 3A6B261F 4C71D5AA
t = 38: 24957F22 43F87AE9 564CFF26 AADF0CBB 3A6B261F
t = 39: ADEB7478 24957F22 50FE1EBA 564CFF26 AADF0CBB
t = 40: D70E5010 ADEB7478 89255FC8 50FE1EBA 564CFF26
t = 41: 79BCFB08 D70E5010 2B7ADD1E 89255FC8 50FE1EBA
t = 42: F9BCB8DE 79BCFB08 35C39404 2B7ADD1E 89255FC8
t = 43: 633E9561 F9BCB8DE 1E6F3EC2 35C39404 2B7ADD1E
t = 44: 98C1EA64 633E9561 BE6F2E37 1E6F3EC2 35C39404
t = 45: C6EA241E 98C1EA64 58CFA558 BE6F2E37 1E6F3EC2
t = 46: A2AD4F02 C6EA241E 26307A99 58CFA558 BE6F2E37
t = 47: C8A69090 A2AD4F02 B1BA8907 26307A99 58CFA558
t = 48: 88341600 C8A69090 A8AB53C0 B1BA8907 26307A99
t = 49: 7E846F58 88341600 3229A424 A8AB53C0 B1BA8907
t = 50: 86E358BA 7E846F58 220D0580 3229A424 A8AB53C0
t = 51: 8D2E76C8 86E358BA 1FA11BD6 220D0580 3229A424
t = 52: CE892E10 8D2E76C8 A1B8D62E 1FA11BD6 220D0580
t = 53: EDEA95B1 CE892E10 234B9DB2 A1B8D62E 1FA11BD6
t = 54: 36D1230A EDEA95B1 33A24B84 234B9DB2 A1B8D62E
t = 55: 776C3910 36D1230A 7B7AA56C 33A24B84 234B9DB2
t = 56: A681B723 776C3910 8DB448C2 7B7AA56C 33A24B84
t = 57: AC0A794F A681B723 1DDB0E44 8DB448C2 7B7AA56C
t = 58: F03D3782 AC0A794F E9A06DC8 1DDB0E44 8DB448C2
t = 59: 9EF775C3 F03D3782 EB029E53 E9A06DC8 1DDB0E44
t = 60: 36254B13 9EF775C3 BC0F4DE0 EB029E53 E9A06DC8
t = 61: 4080D4DC 36254B13 E7BDDD70 BC0F4DE0 EB029E53
t = 62: 2BFAF7A8 4080D4DC CD8952C4 E7BDDD70 BC0F4DE0
t = 63: 513F9CA0 2BFAF7A8 10203537 CD8952C4 E7BDDD70
t = 64: E5895C81 513F9CA0 0AFEBDEA 10203537 CD8952C4
t = 65: 1037D2D5 E5895C81 144FE728 0AFEBDEA 10203537
t = 66: 14A82DA9 1037D2D5 79625720 144FE728 0AFEBDEA
t = 67: 6D17C9FD 14A82DA9 440DF4B5 79625720 144FE728
t = 68: 2C7B07BD 6D17C9FD 452A0B6A 440DF4B5 79625720
t = 69: FDF6EFFF 2C7B07BD 5B45F27F 452A0B6A 440DF4B5
t = 70: 112B96E3 FDF6EFFF 4B1EC1EF 5B45F27F 452A0B6A
t = 71: 84065712 112B96E3 FF7DBBFF 4B1EC1EF 5B45F27F
t = 72: AB89FB71 84065712 C44AE5B8 FF7DBBFF 4B1EC1EF
t = 73: C5210E35 AB89FB71 A10195C4 C44AE5B8 FF7DBBFF
t = 74: 352D9F4B C5210E35 6AE27EDC A10195C4 C44AE5B8
t = 75: 1A0E0E0A 352D9F4B 7148438D 6AE27EDC A10195C4
t = 76: D0D47349 1A0E0E0A CD4B67D2 7148438D 6AE27EDC
t = 77: AD38620D D0D47349 86838382 CD4B67D2 7148438D
t = 78: D3AD7C25 AD38620D 74351CD2 86838382 CD4B67D2
t = 79: 8CE34517 D3AD7C25 6B4E1883 74351CD2 86838382.
A B C D E
t = 0: 2DF257E9 F4286818 B0DEC9EB 0408F581 84677148
t = 1: 4D3DC58F 2DF257E9 3D0A1A06 B0DEC9EB 0408F581
t = 2: C352BB05 4D3DC58F 4B7C95FA 3D0A1A06 B0DEC9EB
t = 3: EEF743C6 C352BB05 D34F7163 4B7C95FA 3D0A1A06
t = 4: 41E34277 EEF743C6 70D4AEC1 D34F7163 4B7C95FA
t = 5: 5443915C 41E34277 BBBDD0F1 70D4AEC1 D34F7163
t = 6: E7FA0377 5443915C D078D09D BBBDD0F1 70D4AEC1
t = 7: C6946813 E7FA0377 1510E457 D078D09D BBBDD0F1
t = 8: FDDE1DE1 C6946813 F9FE80DD 1510E457 D078D09D
t = 9: B8538ACA FDDE1DE1 F1A51A04 F9FE80DD 1510E457
t = 10: 6BA94F63 B8538ACA 7F778778 F1A51A04 F9FE80DD
t = 11: 43A2792F 6BA94F63 AE14E2B2 7F778778 F1A51A04
t = 12: FECD7BBF 43A2792F DAEA53D8 AE14E2B2 7F778778
t = 13: A2604CA8 FECD7BBF D0E89E4B DAEA53D8 AE14E2B2
t = 14: 258B0BAA A2604CA8 FFB35EEF D0E89E4B DAEA53D8
t = 15: D9772360 258B0BAA 2898132A FFB35EEF D0E89E4B
t = 16: 5507DB6E D9772360 8962C2EA 2898132A FFB35EEF
t = 17: A51B58BC 5507DB6E 365DC8D8 8962C2EA 2898132A
t = 18: C2EB709F A51B58BC 9541F6DB 365DC8D8 8962C2EA
t = 19: D8992153 C2EB709F 2946D62F 9541F6DB 365DC8D8
t = 20: 37482F5F D8992153 F0BADC27 2946D62F 9541F6DB
t = 21: EE8700BD 37482F5F F6264854 F0BADC27 2946D62F
t = 22: 9AD594B9 EE8700BD CDD20BD7 F6264854 F0BADC27
t = 23: 8FBAA5B9 9AD594B9 7BA1C02F CDD20BD7 F6264854
t = 24: 88FB5867 8FBAA5B9 66B5652E 7BA1C02F CDD20BD7
t = 25: EEC50521 88FB5867 63EEA96E 66B5652E 7BA1C02F
t = 26: 50BCE434 EEC50521 E23ED619 63EEA96E 66B5652E
t = 27: 5C416DAF 50BCE434 7BB14148 E23ED619 63EEA96E
t = 28: 2429BE5F 5C416DAF 142F390D 7BB14148 E23ED619
t = 29: 0A2FB108 2429BE5F D7105B6B 142F390D 7BB14148
t = 30: 17986223 0A2FB108 C90A6F97 D7105B6B 142F390D
t = 31: 8A4AF384 17986223 028BEC42 C90A6F97 D7105B6B
t = 32: 6B629993 8A4AF384 C5E61888 028BEC42 C90A6F97
t = 33: F15F04F3 6B629993 2292BCE1 C5E61888 028BEC42
t = 34: 295CC25B F15F04F3 DAD8A664 2292BCE1 C5E61888
t = 35: 696DA404 295CC25B FC57C13C DAD8A664 2292BCE1
t = 36: CEF5AE12 696DA404 CA573096 FC57C13C DAD8A664
t = 37: 87D5B80C CEF5AE12 1A5B6901 CA573096 FC57C13C
t = 38: 84E2A5F2 87D5B80C B3BD6B84 1A5B6901 CA573096
t = 39: 03BB6310 84E2A5F2 21F56E03 B3BD6B84 1A5B6901
t = 40: C2D8F75F 03BB6310 A138A97C 21F56E03 B3BD6B84
t = 41: BFB25768 C2D8F75F 00EED8C4 A138A97C 21F56E03
t = 42: 28589152 BFB25768 F0B63DD7 00EED8C4 A138A97C
t = 43: EC1D3D61 28589152 2FEC95DA F0B63DD7 00EED8C4
t = 44: 3CAED7AF EC1D3D61 8A162454 2FEC95DA F0B63DD7
t = 45: C3D033EA 3CAED7AF 7B074F58 8A162454 2FEC95DA
t = 46: 7316056A C3D033EA CF2BB5EB 7B074F58 8A162454
t = 47: 46F93B68 7316056A B0F40CFA CF2BB5EB 7B074F58
t = 48: DC8E7F26 46F93B68 9CC5815A B0F40CFA CF2BB5EB
t = 49: 850D411C DC8E7F26 11BE4EDA 9CC5815A B0F40CFA
t = 50: 7E4672C0 850D411C B7239FC9 11BE4EDA 9CC5815A
t = 51: 89FBD41D 7E4672C0 21435047 B7239FC9 11BE4EDA
t = 52: 1797E228 89FBD41D 1F919CB0 21435047 B7239FC9
t = 53: 431D65BC 1797E228 627EF507 1F919CB0 21435047
t = 54: 2BDBB8CB 431D65BC 05E5F88A 627EF507 1F919CB0
t = 55: 6DA72E7F 2BDBB8CB 10C7596F 05E5F88A 627EF507
t = 56: A8495A9B 6DA72E7F CAF6EE32 10C7596F 05E5F88A
t = 57: E785655A A8495A9B DB69CB9F CAF6EE32 10C7596F
t = 58: 5B086C42 E785655A EA1256A6 DB69CB9F CAF6EE32
t = 59: A65818F7 5B086C42 B9E15956 EA1256A6 DB69CB9F
t = 60: 7AAB101B A65818F7 96C21B10 B9E15956 EA1256A6
t = 61: 93614C9C 7AAB101B E996063D 96C21B10 B9E15956
t = 62: F66D9BF4 93614C9C DEAAC406 E996063D 96C21B10
t = 63: D504902B F66D9BF4 24D85327 DEAAC406 E996063D
t = 64: 60A9DA62 D504902B 3D9B66FD 24D85327 DEAAC406
t = 65: 8B687819 60A9DA62 F541240A 3D9B66FD 24D85327
t = 66: 083E90C3 8B687819 982A7698 F541240A 3D9B66FD
t = 67: F6226BBF 083E90C3 62DA1E06 982A7698 F541240A
t = 68: 76C0563B F6226BBF C20FA430 62DA1E06 982A7698
t = 69: 989DD165 76C0563B FD889AEF C20FA430 62DA1E06
t = 70: 8B2C7573 989DD165 DDB0158E FD889AEF C20FA430
t = 71: AE1B8E7B 8B2C7573 66277459 DDB0158E FD889AEF
t = 72: CA1840DE AE1B8E7B E2CB1D5C 66277459 DDB0158E
t = 73: 16F3BABB CA1840DE EB86E39E E2CB1D5C 66277459
t = 74: D28D83AD 16F3BABB B2861037 EB86E39E E2CB1D5C
t = 75: 6BC02DFE D28D83AD C5BCEEAE B2861037 EB86E39E
t = 76: D3A6E275 6BC02DFE 74A360EB C5BCEEAE B2861037
t = 77: DA955482 D3A6E275 9AF00B7F 74A360EB C5BCEEAE
t = 78: 58C0AAC0 DA955482 74E9B89D 9AF00B7F 74A360EB
t = 79: 906FD62C 58C0AAC0 B6A55520 74E9B89D 9AF00B7F.
FIPS PUB 180-1
FEDERAL INFORMATION
PROCESSING STANDARDS PUBLICATION
1995 April 17
U.S. DEPARTMENT OF COMMERCE/National Institute of Standards and
Technology